Security Risk Assessment: Managing Physical and Operational Security

A security risk assessment is a critical step in protecting your organization from security threats. It helps you identify, assess, and mitigate risks to your physical and operational security. By understanding the risks that your organization faces, you can take steps to protect your assets, your employees, and your reputation.
There are many reasons why a security risk assessment is important. Some of the benefits include:
- Identify risks: A security risk assessment helps you identify the risks that your organization faces. This includes both internal and external risks, such as natural disasters, cyberattacks, and theft.
- Assess risks: Once you have identified the risks that your organization faces, you need to assess their likelihood and impact. This will help you prioritize your security efforts and focus on the most critical risks.
- Mitigate risks: Once you have assessed the risks that your organization faces, you need to develop and implement mitigation strategies. These strategies should be designed to reduce the likelihood and impact of the risks.
- Monitor risks: The security landscape is constantly changing, so it is important to monitor your risks on an ongoing basis. This will help you identify new risks and make sure that your mitigation strategies are still effective.
There are many different types of risks that can affect your organization's physical and operational security. Some of the most common risks include:
4.2 out of 5
| Language | : | English |
| File size | : | 2597 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 213 pages |
- Natural disasters: Natural disasters, such as earthquakes, floods, and hurricanes, can cause significant damage to your physical assets and disrupt your operations.
- Cyberattacks: Cyberattacks, such as hacking and malware, can compromise your computer systems and networks, and can lead to the theft of sensitive data.
- Theft: Theft is the unauthorized taking of property. This can include the theft of physical assets, such as equipment and inventory, or the theft of intellectual property, such as trade secrets and customer data.
- Sabotage: Sabotage is the intentional damage or destruction of property. This can be motivated by a variety of factors, such as revenge, terrorism, or industrial espionage.
- Terrorism: Terrorism is the use of violence or the threat of violence to achieve political or religious goals. Terrorism can have a significant impact on your organization's physical and operational security.
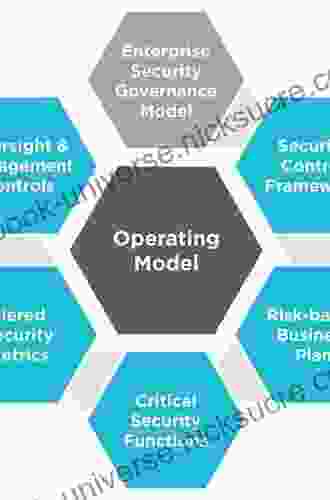
The following steps are involved in conducting a security risk assessment:
- Identify assets: The first step is to identify the assets that you need to protect. This includes your physical assets, such as your buildings, equipment, and inventory, as well as your intangible assets, such as your data, your reputation, and your goodwill.
- Identify threats: The next step is to identify the threats that could potentially harm your assets. This includes both internal and external threats, such as natural disasters, cyberattacks, and theft.
- Assess risks: Once you have identified the threats that your organization faces, you need to assess their likelihood and impact. This will help you prioritize your security efforts and focus on the most critical risks.
- Develop mitigation strategies: Once you have assessed the risks that your organization faces, you need to develop and implement mitigation strategies. These strategies should be designed to reduce the likelihood and impact of the risks.
- Monitor risks: The security landscape is constantly changing, so it is important to monitor your risks on an ongoing basis. This will help you identify new risks and make sure that your mitigation strategies are still effective.
There are a number of best practices that you can follow to manage your physical and operational security. Some of these best practices include:
- Implement physical security measures: Physical security measures, such as fences, gates, and security cameras, can help to deter and prevent unauthorized access to your property.
- Implement operational security measures: Operational security measures, such as access control and security awareness training, can help to protect your organization from internal and external threats.
- Conduct regular security audits: Regular security audits can help you to identify vulnerabilities in your security system and make sure that your mitigation strategies are still effective.
- Have a security plan in place: A security plan outlines the steps that you will take in the event of a security incident. Having a security plan in place will help you to respond quickly and effectively to a security incident.
A security risk assessment is a critical step in protecting your organization from security threats. By understanding the risks that your organization faces, you can take steps to protect your assets, your employees, and your reputation.
By following the best practices for managing physical and operational security, you can help to reduce the likelihood and impact of security incidents.
4.2 out of 5
| Language | : | English |
| File size | : | 2597 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 213 pages |
Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
 Best Book Source
Best Book Source Ebook Universe
Ebook Universe Read Ebook Now
Read Ebook Now Digital Book Hub
Digital Book Hub Ebooks Online Stores
Ebooks Online Stores Fiction
Fiction Non Fiction
Non Fiction Romance
Romance Mystery
Mystery Thriller
Thriller SciFi
SciFi Fantasy
Fantasy Horror
Horror Biography
Biography Selfhelp
Selfhelp Business
Business History
History Classics
Classics Poetry
Poetry Childrens
Childrens Young Adult
Young Adult Educational
Educational Cooking
Cooking Travel
Travel Lifestyle
Lifestyle Spirituality
Spirituality Health
Health Fitness
Fitness Technology
Technology Science
Science Arts
Arts Crafts
Crafts DIY
DIY Gardening
Gardening Petcare
Petcare Bruce Chilton
Bruce Chilton Isabella Tree
Isabella Tree William F Buckley Jr
William F Buckley Jr William O Connor
William O Connor Kikuko Otake
Kikuko Otake John P Parker
John P Parker Jack Couffer
Jack Couffer Randy Thompson
Randy Thompson Eric Bailey
Eric Bailey Ed Ayres
Ed Ayres Kristin Linklater
Kristin Linklater Carlo Ancelotti
Carlo Ancelotti Joseph Boyden
Joseph Boyden Natalia Sobrevilla Perea
Natalia Sobrevilla Perea Suzanne Carreiro
Suzanne Carreiro Immaculee Ilibagiza
Immaculee Ilibagiza Marilyn Wenzke Nickels
Marilyn Wenzke Nickels Richard King
Richard King Sarah Ruhl
Sarah Ruhl Martha Helena Ortiz Arenas
Martha Helena Ortiz Arenas
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Henry Wadsworth LongfellowGrowing Up in India: The Invisible Struggles of the Most Backward Caste
Henry Wadsworth LongfellowGrowing Up in India: The Invisible Struggles of the Most Backward Caste Herman MelvilleFollow ·14.7k
Herman MelvilleFollow ·14.7k Edward ReedFollow ·2.5k
Edward ReedFollow ·2.5k Herb SimmonsFollow ·6.1k
Herb SimmonsFollow ·6.1k Tim ReedFollow ·6.2k
Tim ReedFollow ·6.2k Patrick RothfussFollow ·8.8k
Patrick RothfussFollow ·8.8k Evan HayesFollow ·6.4k
Evan HayesFollow ·6.4k Chinua AchebeFollow ·8.2k
Chinua AchebeFollow ·8.2k Keith CoxFollow ·11k
Keith CoxFollow ·11k

 Dallas Turner
Dallas TurnerThe Race to Control Cyberspace: Bill Gates's Plan for a...
Bill Gates has a...

 Clayton Hayes
Clayton HayesMy 40 Year Career On Screen And Behind The Camera
I've been working in...

 Arthur Mason
Arthur MasonUniquely Dangerous: The Troubling Record of Carreen...
Carreen Maloney, a Democratic...

 Floyd Richardson
Floyd RichardsonThe True Story of a Canadian Bomber Pilot in World War...
In the annals of World...

 Corey Hayes
Corey HayesThe Sky of Youth: A Journey of Discovery and Fulfillment
By John Maxwell ...

 Truman Capote
Truman CapoteThe Great Central Bank Experiment: Finance Matters
Central banks have been...
4.2 out of 5
| Language | : | English |
| File size | : | 2597 KB |
| Text-to-Speech | : | Enabled |
| Screen Reader | : | Supported |
| Enhanced typesetting | : | Enabled |
| Word Wise | : | Enabled |
| Print length | : | 213 pages |